Security Warnings and Alerts
This page contains any current (and past) online issues that we are aware of, and may be of a security concern to our users and citizens. We have this information available so as to be as transparent with the public, and our users, as we can. It has been posited that making this information available makes us less secure, on the contrary it helps us be more secure by "keeping us honest" not only with the public, but with ourselves. So we continue to strive to be more secure.
Daily we do see probing of our Web facing servers, as is the case with every server on the internet. So far we have been fortunate that any internet security issues that involve the City of Canton have been few and far between, we do our best to keep our networks and servers secure and to keep up with current security concerns.
If you know of any communication that says it is from the City of Canton but it seems illegitimate, feel free to contact the to verify its authenticity.
Remember to always take your online security seriously and be suspicious of any unexpected e-mails, messages, phone calls, or texts that you receive. Your personal information is very valuable and should be protected by you and by anyone you entrust it to.
To someone with nefarious intentions, your personal information has monetary value that they can quickly exploit. At the same time they can turn your life upside down for weeks or months while you try to undo any of the bad things they have done.
End 2019 - Begin 2020
As the year 2019 was coming to a close and in the beginning of 2020, the Information Technology (IT) Department noticed a substantial increase in Spear Phishing attacks targeted on the City of Canton. IT has now mandated that all City email accounts be protected with Two Factor Authentication (2FA). All of the City's users email accounts are now using 2FA. No City email accounts are known to have been compromised, but we are seeing phishing (and spear phishing) emails being sent as though they are coming from City employees (but if you check the actual email address that the email comes from, it is not from the user they say it is from).
Around the world there has also been a huge increase in Crypto Ransomware, the main targets seem to be cities, counties, schools, airports, and hospitals (among others like them). The targets seem to be chosen because they can pay out larger amounts of money in order to get their systems working again.
Everyone should take their online security very seriously. Be vigilant in checking out any email that you receive if you were not expecting it to come to you. Check the email addresses in the header of the emails to make sure they seem to be coming from whom they say they are coming from. You should also check (and double check) any links in the email that you are being asked to follow, make sure they are going where you expect them to go to. If you feel like anything is not right in the email, maybe it just gives you a funny feeling, call the sender using a phone number you already have for them and ask them to verify that the email is a legitimate email from them. In the world today it is alright to be suspicious of emails that you receive.
September 6, 2019
On September 6, 2019, the City of Canton was the target of an email Spear Phishing attack.
One of the City of Canton's employees was sent the following email:
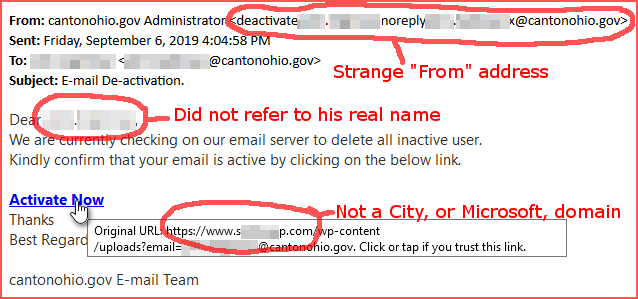
The user didn't give his information to the Phishing site, and he forwarded the email to the IT Department!
The City of Canton's employees are being advised to NOT follow links on suspicious emails, or enter any information on unfamiliar domains.
This Phishing email is very similar to the June 28, 2018, Phishing email below, but a little more polished.
City employees are continuing to be targets of Phishing attacks, probably being conducted by adversarial state level actors, such as Russia, China, and North Korea. City employees need to stay alert and vigilant in the fight against these attacks, because the attacks are not going to end, and they still seem to be increasing.
January 9, 2019
On January 9, 2019, a user in the City's network had a virus on their computer that sent out SPAM and/or Phishing Attack emails.
The City's IT staff was quick to identify that there was an issue, and to take steps to fix the problem.
The City of Canton's employees are being advised to NOT follow links on suspicious emails, or enter any information on unfamiliar domains, even if the email they received is from someone they trust.
If you are not expecting an email from a particular user then you should at least be suspicious of the email's contents, confirm with the user that they sent the email.
June 28, 2018
On June 28, 2018, the City of Canton was the target of an email Spear Phishing attack.
One of the City of Canton's employees was sent the following email:
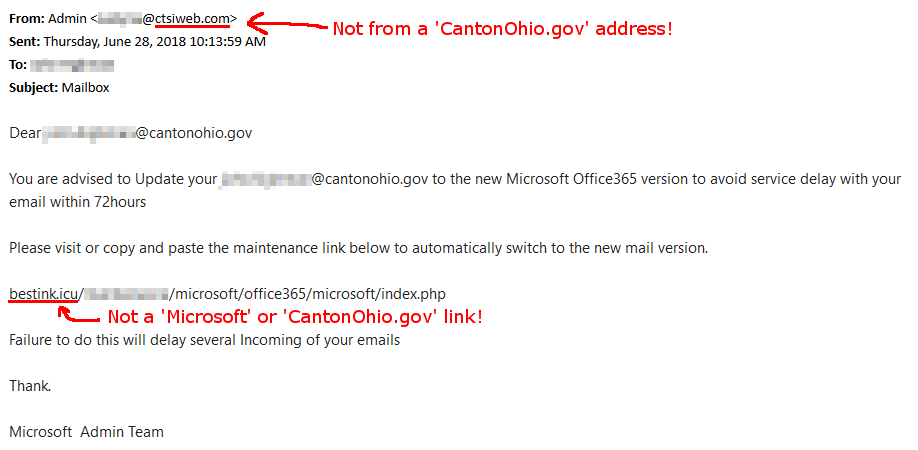
The user must have eaten his WHEATIES™ that morning because he knew it seamed fishy (pun intended), so he forwarded the email to the IT Department!
The City of Canton's employees are being advised to NOT follow links on suspicious emails, or enter any information on unfamiliar domains.
City employees are continuing to be targets of Phishing attacks, probably being conducted by adversarial state level actors, such as Russia, China, and North Korea. City employees need to stay alert and vigilant in the fight against these attacks, because the attacks are not going to end, and they seem to be increasing in this last year.
May 22, 2018
On May 22, 2018, the City of Canton was the target of an email Spear Phishing attack.
One of the City of Canton's employees was sent the following email:
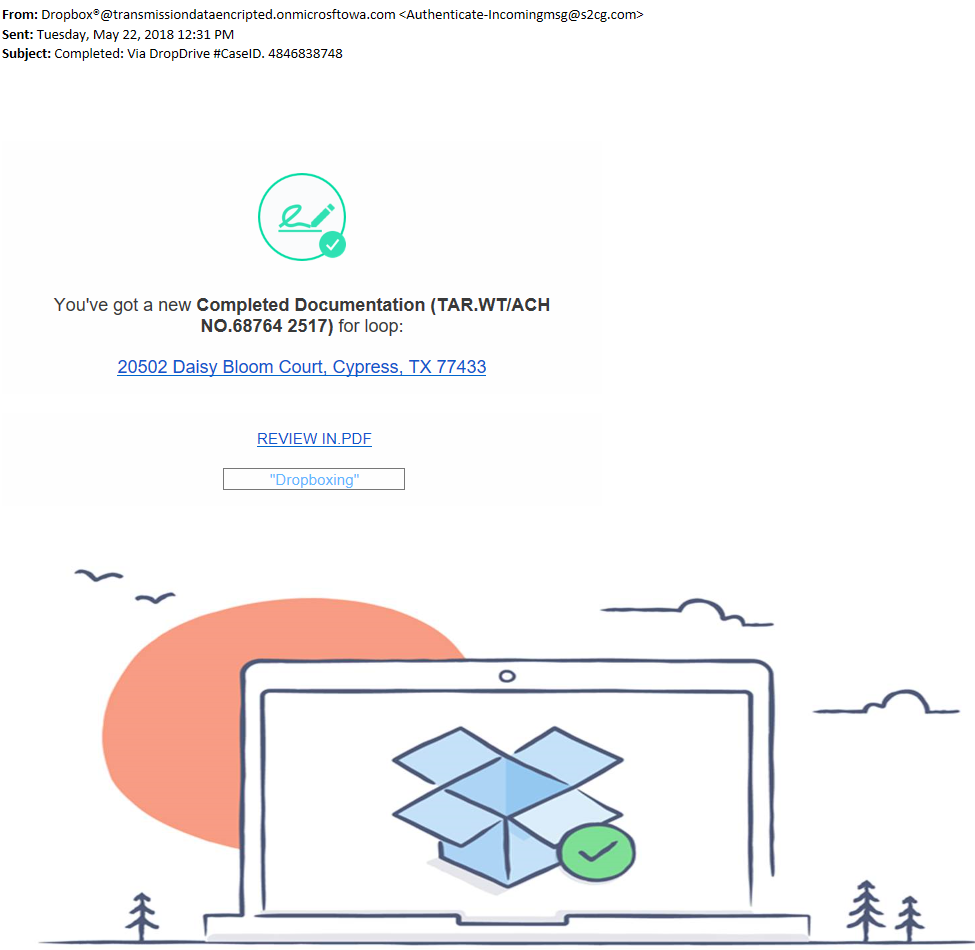
Unfortunately the email looked like something the user was expecting and the user clicked on its link and entered the user name/password into the subsequent screens that came up and looked like the City's email login page. The site that he was forwarded to was on a different domain than the City's employees log in on, which should be the first clue to the users that it was not a legitimate email, and users should recognize the sender's name on the email!
The City of Canton's employees are being advised to NOT follow the link on the email, or enter any information on unfamiliar domains.
The City's employee realized almost immediately they entered information on a malicious web site and quickly changed the password before the account was compromised.
April 2, 2018
On April 2, 2018, the City of Canton was the target of an email Phishing attack.
Many of the City of Canton's employees were sent the following email:
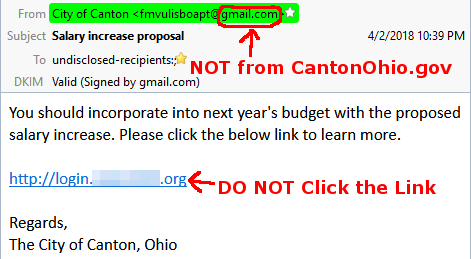
The email was sent from a Gmail account, which should be the first clue to the users that it was not a legitimate email from the City's IT Department, official emails will only come from CantonOhio.gov email addresses, and the users should recognize the sender's name!
The City of Canton's employees are being advised to NOT follow the link on the email.
If any of the City's employees have followed the link and entered information on the site then they NEED TO CONTACT The City of Canton's IT Hot Line, IMMEDIATELY! They also NEED TO CHANGE ANY AND ALL PASSWORDS that they think might be the same as the information they entered on the bad web site! That applies to any personal (social/financial/shopping/etc.) sites that they visit.
As a security precaution, we are temporarily only allowing users to log in to the City's Web site from Trusted IP addresses.
February 9, 2018
Starting on February 9, 2018, the City of Canton's internal network was infected with a virus. At the time the City did not know the extent that the virus could propagate. The virus spread without user interaction via zero-day vulnerabilities in the Windows networking ports.
The virus was designed to go out to the internet to get instructions from the hacker that created it. Thankfully the way the City's networks are designed and managed, it was not able to get instructions from its creator. So all it could do was spread, and not do any damage or exfiltrate any information.
The City worked with its antivirus providers to make progress in eradicating the virus from the network.
November 3, 2017
On November 3, 2017, the City of Canton was the target of an email Spear Phishing attack.
Many of the City of Canton's employees were sent the following email:
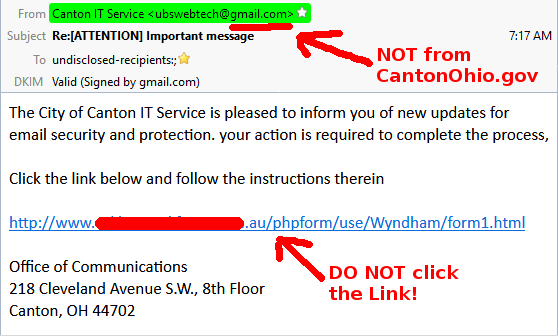
The email was sent from a Gmail account, which should be the first clue to the users that it was not a legitimate email from the City's IT Department, official emails will only come from CantonOhio.gov email addresses, and the users should recognize the sender's name!
The City of Canton's employees are being advised to NOT follow the link on the email.
If any of the City's employees have followed the link and entered information on the site then they NEED TO CONTACT The City of Canton's IT Hot Line, IMMEDIATELY! They also NEED TO CHANGE ANY AND ALL PASSWORDS that they think might be the same as the information they entered on the bad web site! That applies to any personal (social/financial/shopping/etc.) sites that they visit.
As a security precaution, we are temporarily only allowing users to log in to the City's Web site from Trusted IP addresses.
June 25, 2017
On June 25, 2017, several Ohio State Government web sites were defaced, the hackers made use of exploits that target un-patched Windows Operating System servers. We have received a few comments and questions from the public and outside entities regarding these hacks, so we decided to address them here.
The City of Canton's web facing servers are currently running Linux Operating Systems and are not able to be compromised using the methods that were used on the State's computers.
The City of Canton's web sites also undergo regular 3rd party security scans for known vulnerabilities, such as the ones mentioned above, and the City hasn't had any vulnerabilities show up since 2008 (and that was just a warning that a page could display sanitized [non-harmful] text that was submitted by a user). We also try to keep up-to-date on current security issues and proactively make any changes that are needed prior to there being an incident.
None of the City's I.T. Department managed servers with direct access from the internet are known to be vulnerable (we can't speak for servers managed by outside entities). None of the City's I.T. Department managed servers were compromised.
September 26, 2014
On September 12, 2014, a vulnerability (or 'bug') was discovered and disclosed on September 24, 2014. That bug is called 'Shellshock' (and sometimes 'Bashdoor').
It is a bug in the Unix Bash shell (or 'Bourne Shell'), which is kind of like a command line on a computer.
The first bug causes Bash to unintentionally execute commands when the commands are concatenated to the end of function definitions stored in the values of environment variables. Within days of the publication of this, intense scrutiny of the underlying design flaws discovered a variety of related vulnerabilities, which were addressed with a series of further patches.
Attackers exploited Shellshock within hours of the initial disclosure by creating botnets of compromised computers to perform distributed denial-of-service attacks and vulnerability scanning. Security companies recorded millions of attacks and probes related to the bug in the days following the disclosure.
Shellshock could potentially compromise millions of unpatched servers and other systems. Accordingly, it has been compared to the Heartbleed bug in its severity.
Only Unix (and Linux) servers that run the vulnerable version of Bash, and that have direct connections to the internet, may have been compromised. The City of Canton did find one server that was vulnerable, it was patched as the patches became available. None of the City's servers were compromised.
April 15, 2014
Last week news was disclosed about a Secure Sockets Layer (SSL)* vulnerability in the OpenSSL library* that is used by some Apache web servers, they have dubbed the vulnerability 'Heartbleed'.
This vulnerability is found in OpenSSL versions 1.0.1 through 1.0.1f, and 1.0.2 beta.
Any server running any of those versions should be immediately upgraded to OpenSSL version 1.0.1g or 1.0.2 beta 2, and obtain a new SSL certificate.
We have checked all of our servers that use SSL, and have found that none of our servers have ever been affected by this bug.
We are confident that our servers and all users of our sites were not exploited by the Heartbleed vulnerability.
* Nontechnical Definitions:
Secure Sockets Layer (SSL) - a communication protocol computers use to take information, encrypt it, transport it across a network or the internet, and decrypted it on another computer.
library - a software library basically contains software that is not used by users directly, but by other programs.
NOTE: Our "Nontechnical Definitions" are only meant to give nontechnical people a hint of what the word or phrase actually means in the context it was used in, they are not official definitions.
August 12, 2013
It has come to our attention that somebody is sending an e-mail claiming to be from the City of Canton with an e-mail address of '[email protected]' and asking for some personal information. Do not respond to it, it is NOT from the City of Canton.
Here is the text of that fake email:
WE WERE DIRECTED TO FORWARD THIS MESSAGE TO YOU. TAKE THIS VERY SERIOUSLY
AND KEEP THE DETAILS CONFIDENTIAL:
WE HAVE IN OUR CUSTODY FUND LEFT BEHIND TO YOUR FAMILY BY A LATE RELATIVE.
GET BACK TO US IMMEDIATELY FOR COMPLETE INFO. PLEASE PROVIDE THE FOLLOWING
DETAILS NOW FOR VERIFICATION SO THAT WE CAN FORWARD FURTHER DETAILS.
(1)FIRST NAME:.........(2)LAST NAME:.........(3)POSTAL ADDRESS:......../
(4)DIRECT MOBILE NUMBER:......THANKS.
Update:
This e-mail has a spoofed 'FROM' e-mail address (noted above) which was never a real e-mail address for us or the attacker, and it has a different 'REPLY-TO' e-mail address which usually stays hidden until the recipient clicks the 'Reply' button. This is a fairly simple thing to accomplish, it can be done within most e-mail clients (ex. Outlook, Thunderbird, etc.) and it can also be accomplished programmatically.
The 'REPLY-TO' e-mail address in this scenario is a 'disposable' e-mail address that is set up by the attacker and it will usually bounce your reply through several other e-mail addresses (most often in different countries to make it more difficult to track down the real person[s]). The 'disposable' e-mail address is usually abandoned after a few days.
The City of Canton network and servers have not been compromised and it does not seem like the fraudulent e-mail was 'bounced' though the City's e-mail servers.
If you or any one you know has received an unexpected and suspicious e-mail that claims to be from the City of Canton, please forward it to the e-mail address. Once we get it we can determine if it is valid or fraudulent.
Any new security concerns (that could effect the public and our technological infrastructure) we become aware of will be listed near the top of this page.


